Scalingo's guide: How to choose the best VPN for your company

If you need to ensure the confidentiality of the data communication between servers you may be looking for the best VPN software solution that suits your needs.
In this article, we will share our experience and will help you to choose the best VPN for you and your company.
Our experience at Scalingo
Operators of Scalingo’s production platform have to connect to servers to perform maintenance operations.
They connect to the servers using the SSH protocol through a server called Bastion, which allows filtering of accesses, in addition to the authentication of the SSH protocol itself.
To reach a new compliance level we decided that the connections of Scalingo's operators to the application hosting servers must get an extra layer of security. That's why we implemented a VPN solution.
The VPN solution implemented for this case is a remote access VPN using strongSwan solution (IPsec / IKEv2).
We realized that choosing a VPN for a company can be challenging, and we are going to share with you how we proceeded with finding a solution that suits our security, compatibility, and ease of use requirements.
You will find our reasoning behind this choice in the following article.
What is a VPN?
The word VPN stands for Virtual Private Network, and it allows users to extend a private network across a public network.
This system creates a direct link between different remote devices and isolates their exchanges from the rest of the traffic of public networks.
Users and devices that are connected to it, are able to send and receive data over this private network provided by the VPN while being connected to a public or shared network.
All VPNs offer a variety of different security features which ensure that the connection and data transiting through the VPN over the public network is encrypted from end-to-end.
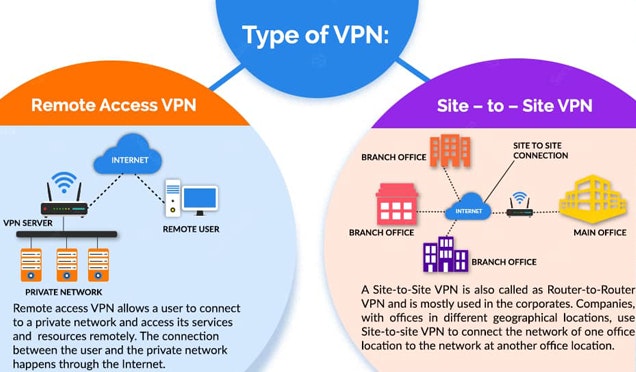
There are mainly two types of VPNs that are used, depending on the needs.
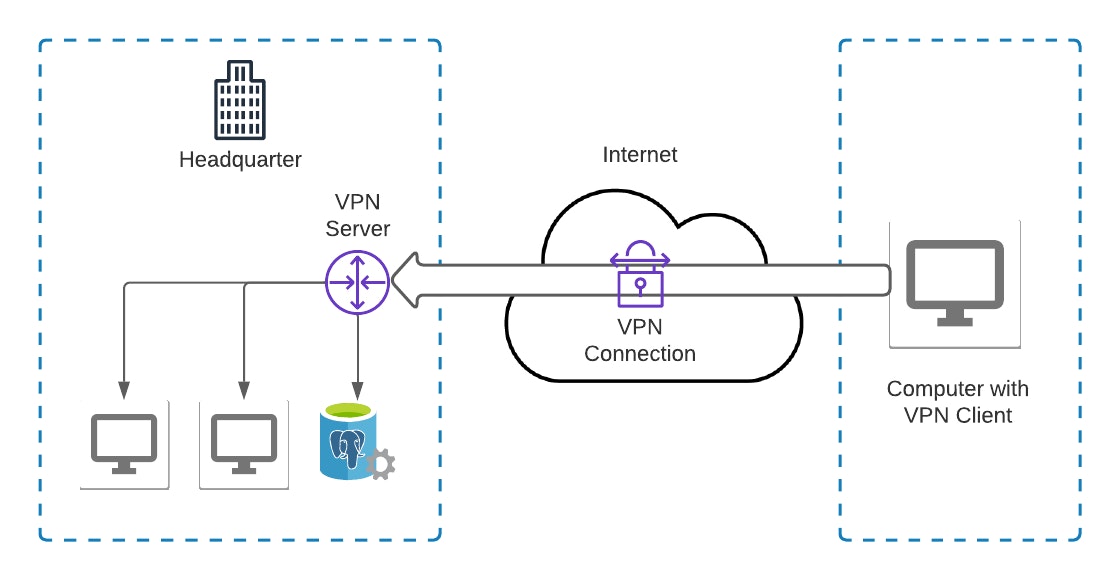
Remote Access VPN (or Client-to-site)
The Remote Access/Client-to-Site VPN can be used from anywhere, regardless of the network.
It allows access to a private network through the Internet. This is the most common type of VPN seen on the internet. It can be used for both personal and professional use.
This type of VPN regularly requires a client to connect to the remote VPN server over the Internet.
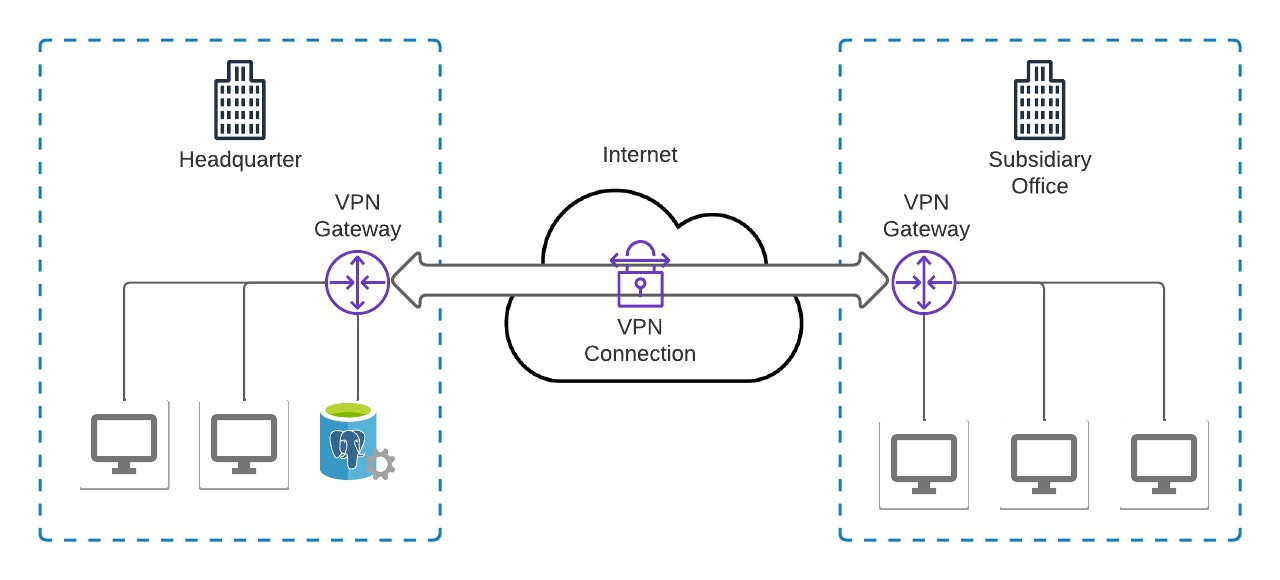
Site-to-site
The Site-to-Site VPN can only be used on networks that have been predefined in the set-up phase.
It allows you to be in the private network while going through the internet securely. There is no need to have a VPN client installed on the PC as the VPN connection is managed on the network (router side) to which devices like a computer are connected.
This type of VPN is widely used in medium and large companies. Especially to have a private network between distant locations (offices, agencies, ...) of a company.
Why do you need a VPN for your company?
When it comes to operations, a VPN for company use is no different from a personal use VPN. The main difference however is that a corporate VPN is designed for business use and is meant to be used by a team.
As for the reasons why you would need a VPN, it will depend essentially on your situation and your specific needs.
For example, you may want to use a VPN if you need to connect to your private network from any location possible.
Or, if you need to allow access to your network from several locations/offices around the world.
How to define your needs for a VPN?
Setting up a VPN may involve some critical problems if it’s not well thought out and prepared.
Many solutions exist, but it’s important to first ask yourself some key questions before making your final choice.
For example, here is a non-exhaustive list of questions that we consider crucial when it comes to choosing a VPN :
- What is the expected reliability? Is a potential disconnection workable or is it critical?
- What operating system should the client run on? Will the users be on macOS, Windows, and/or Linux?
- What is the expected level of security? Should the client run in kernel space/user space? What cryptography algorithms are being used?
- Can it be a SaaS? Or must it be self-hosted?
- Can we perform maintenance operations using it?
- Is managing users an important aspect of your use?
Indeed, specifying your needs is an essential step of this process in order to avoid any potential problems that can happen in the future.
For example, let’s say that you use a VPN to connect to the production servers, but the monitoring probes report a problem with a server.
The operator must be able to connect quickly to the servers hosting the applications, but the VPN server does not respond, takes time to load or the connection is unstable. The operator will find himself stuck in a situation where he is unable to act fast enough or will be blocked by this situation.
In this case, it is clear that the VPN has an important role, so it is critical to ensure the high availability of the VPN service.
There isn’t a unique solution for everyone and every use case. Therefore, you should consider defining your needs in order to find the right VPN for you.
Which VPN to choose?
Depending on the type of VPN you’ve decided to go for, you will now have a wide choice of solutions that exists, and that vary from each other in terms of features.
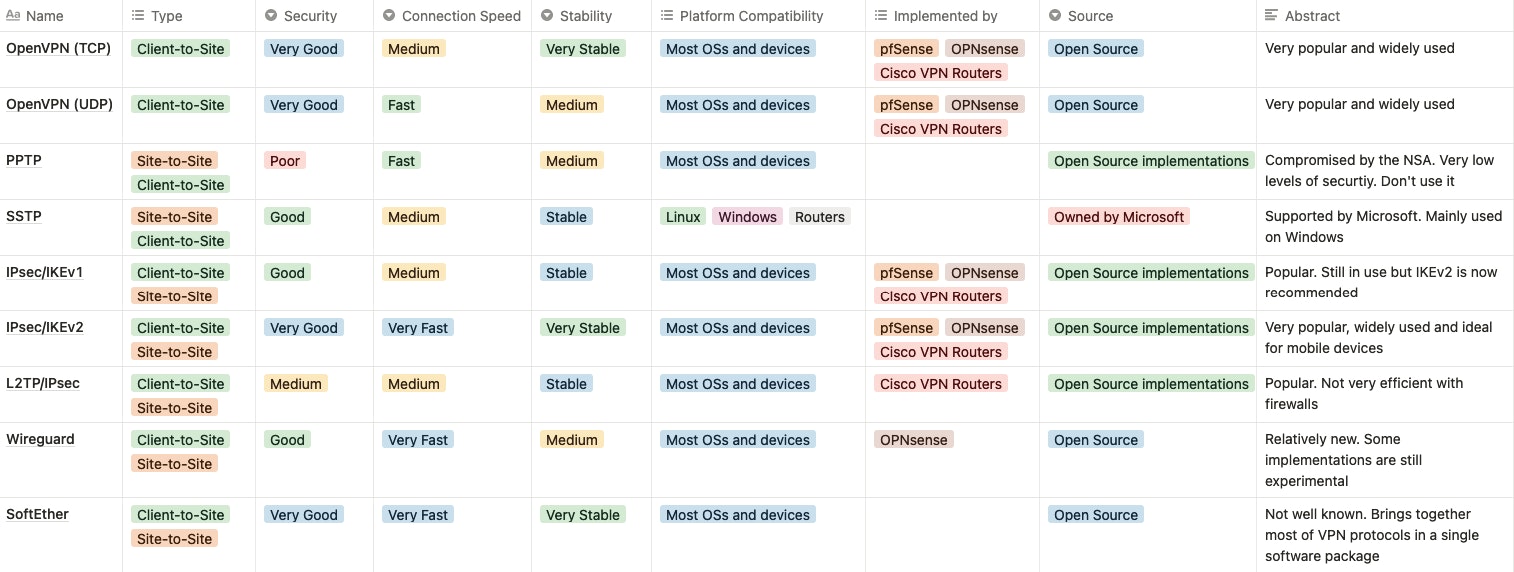
Here is a subjective comparison list that the tech team at Scalingo created to compare different VPN solutions depending on criteria such as security, connection speed, stability, and more:
What did we choose at Scalingo?
At Scalingo we chose the IPsec implementation named strongSwan to set up a remote access VPN, as said before.
The reasons why we chose this solution instead of another one were various, but they were thought after keeping in mind our main needs and requirements:
- The solution must be a Remote Access (Client to Site) VPN
- The solution must be based on IPsec based on the recommendations made by ANSSI (French National Agency for the Security of Information Systems).
- The solution must work on Linux but if it supports other platforms it’s better
- The solution must use strong cryptography algorithms
There are other software implementations of IPsec that exists:
- Openswan2: Seems to not maintained anymore
- Libreswan: A fork of Openswan, maintained, but doesn’t have a lot of internal VPN features
- strongSwan: Well maintained, quite popular, great documentation, natively supports high availability and other nice features
Conclusion
In conclusion, there is a certain number of parameters to take into count when choosing a VPN for your company. The final choice will depend mainly on the specific needs that you have and the features that you are looking for.
However, we mainly recommend strongSwan as a VPN solution based on the IPsec protocol.
Another solution can also be OpenVPN which is also known and easier to set up, but it is not based on IPsec.
Alternatively, Wireguard, which is more recent and not based on IPsec nor on OpenVPN, can be an interesting choice.
At Scalingo we do not offer VPN server hosting. However, we do have VPN connectors that allow you to connect to your remote applications through an encrypted tunnel.
We currently offer the following VPN connectors on Scalingo: