Announcing Scalingo OpenVPN Addon: An Easy Way To Connect Your Private Infrastructure

We are glad to announce the release of a new addon on the platform: Scalingo OpenVPN. Connecting your application containers to your private infrastructure using an encrypted tunnel with OpenVPN is now possible and with the ease you are used to on Scalingo.
Context
A while back, some customers wanted to reach their private infrastructure with a VPN. To respond to this need, the Scalingo VPN IPSec addon has been integrated to the platform.
Because you'll never know what kind of VPN software installation you'll find in the wild (usually you set only one), we're releasing today the new Scalingo OpenVPN addon.
After adding the VPN configuration, all the containers of the application using the addon acquire encrypted connectivity to the targeted private infrastructure.
How does it work?
Your application is running in one or several Docker containers. By default these containers are connected to the external world with one network interface. When the VPN addon is used, a second network interface is automatically created for the VPN connectivity. The following schema represents this method.
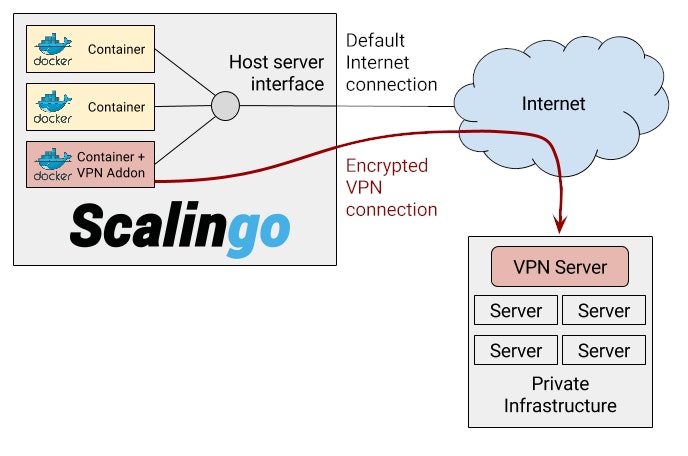
This operation is done before your application is started to ensure the private network is ready when this last is running. If the VPN tunnel fails to start, the application boot will be considered as a failure and the configuration of the VPN should be udpated before attemping again to start new containers.
Security consideration
One of the first question you may be asking yourself is: “how safe is it?”. The platform is ensuring that the VPN interface is only present inside the network namespace of your application containers. A network namespace is an isolated virtual network environment linked to a container. It contains all the network interfaces dedicated to this precise container. It means that for other containers sharing the same host, there is no way to see or sniff anything related to your VPN.
Differences between L2TP/IPsec and OpenVPN technologies
OpenVPN is an open-source VPN solution based on the SSL/TLS encryption protocol. It is highly configurable as it can run on any port and either in TCP or UDP.
L2TP/IPsec implementations are more often closed-source as the most common implementations have been developed by Cisco and Microsoft. They have to run in UDP on the port 500.
It is often considered that OpenVPN, by its leverage of TLS can be configured to be much more secure. A wider variety of encryption algorithms and ciphers are available. Performance is also better with OpenVPN as L2TP/IPSec is encapsulating twice the data (once for encryption, and once for the tunneling).
Configuration
Once the OpenVPN addon has been provisioned, it should be configured through its dashboard. The following items can be configured: OpenVPN, CA Certificate, User Certificate, User Private Key, User Private Key Passphrase, Username/Password.
As stated in their description, these fields should be filled according to the OpenVPN Server configuration. You should ask the administration of the VPN to give you this description.
You can find exhaustive instructions and configuration bits in the Scalingo VPN addon documentation page.
Once validated, your app containers will be automatically restarted, and their logs should contain:
-----> Starting OpenVPN connection…
Socket Buffers: R=[87380->131072] S=[16384->131072]
OpenVPN 2.3.2 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [EPOLL] [PKCS11] [eurephia] [MH] [IPv6] built on Jun 22 2017
Attempting to establish TCP connection with [AF_INET]<IP:PORT> [nonblock]
TCP connection established with [AF_INET]<IP:PORT>
TCPv4_CLIENT link remote: [AF_INET]<IP PORT>
TCPv4_CLIENT link local: [undef]
TLS: Initial packet from [AF_INET]<IP PORT>, sid=a0081f01 2f804579
Data Channel Encrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Control Channel: TLSv1, cipher TLSv1/SSLv3 DHE-RSA-AES256-SHA, 2048 bit RSA
[<remote host>] Peer Connection Initiated with [AF_INET]<IP:PORT>
Data Channel Decrypt: Cipher 'AES-256-CBC' initialized with 256 bit key
Data Channel Encrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
Data Channel Decrypt: Using 256 bit message hash 'SHA256' for HMAC authentication
SENT CONTROL [dpr-scafw01]: 'PUSH_REQUEST' (status=1)
ROUTE_GATEWAY 172.17.0.1/255.255.0.0 IFACE=eth0 HWADDR=02:42:ac:11:00:10
/sbin/ip addr add dev tun0 local <local VPN IP> peer <remote VPN IP>
TUN/TAP TX queue length set to 100
TUN/TAP device tun0 opened
/sbin/ip link set dev tun0 up mtu 1500
do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0
OPTIONS IMPORT: timers and/or timeouts modified
OPTIONS IMPORT: route options modified
/sbin/ip route add <gateway>/32 via 172.17.0.1
Initialization Sequence Completed
/sbin/ip route add <private network> via <remote VPN IP>
-----> OpenVPN connected
Pricing
The Scalingo OpenVPN addon follows the same pricing as the Scalingo VPN IPSec addon: at the moment, there's only one plan that costs 30€/month. We'll see later if new plans are needed.
Conclusion
With our two VPN related addons, Scalingo VPN IPSec and Scalingo OpenVPN, we have a robust toolbox to target nearly any private infrastructure you may have hidden in your company's network. Therefore it's possible to deploy your fast growing apps that needs flexible lifecycles (start, stop, scale up, scale down) on Scalingo and profit from all the goodness of our PaaS (Platform as a Service) without the need of moving everything out of your private datacenters.



