Scalingo MongoDB: now with TLS and internet direct access

We are really proud to release today a feature that will greatly increase your Scalingo MongoDB databases security: TLS encryption. With this new security layer in place, it's now also possible to expose your database on the internet if you wish to do so.
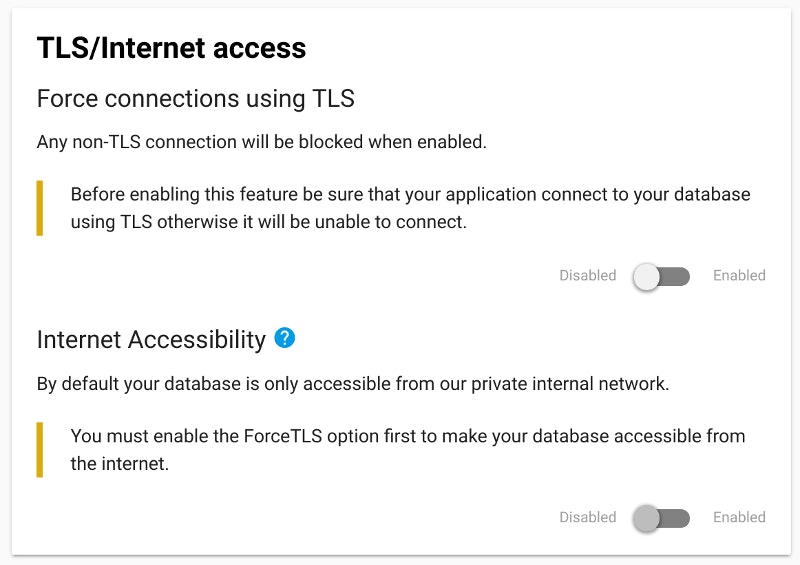
Since the beginning of Scalingo, we were protecting your Scalingo MongoDB databases from the evil internet by hiding them inside our secure network. To access them you had to setup an SSL tunnel with our command line client. Since today, all Scalingo MongoDB databases are shipped with TLS enabled. You can now choose to expose them on the internet, if, and only if, you force TLS only connections.
What is TLS?
Transport Layer Security (TLS) is a cryptographic protocol that provide security for communications over a network. It is also known as Secure Sockets Layer (SSL), its predecessor name.
When secured by TLS, the communication between the client and the server can have one or more of these three properties:
- The communication is private (i.e. nobody can spy the content of your communication).
- Your communication's integrity is guaranteed (i.e. nobody can modify the content of your communication without you knowing it).
- The identities of both parties (client and server) can be authenticated
TLS for MongoDB
MongoDB support TLS to encrypt all of MongoDB's network traffic: either between the client and the server or between the different replicas of your database.
By default, all new MongoDB databases have TLS activated. If you want to
connect to it, just use the --ssl option:
mongo --ssl --sslAllowInvalidCertificates "<connection string>"
For existing databases, activating TLS is a matter of restarting the database. Any action leading to the restart will activate TLS (e.g. plan update, upgrade of the database).
TLS is just an option, you can still access your database without it if needed.
The --sslAllowInvalidCertificates option is mandatory as the generated
certificates for your databases are
self-signed. If you
want the certificate to be trust-able, you need to download our certification
authority certificate and specify it to the MongoDB CLI tool.
Download the CA certificate
The certificate of our certification authority is available on the database dashboard.
After downloading it, you can specify its path to the mongo CLI:
mongo --ssl --sslCAFile=./ca.pem "<connection string>"
DB available from anywhere
From the beginning of Scalingo history, we wanted to protect the communication between your computer and the database from prying eyes. By default access to most databases are unencrypted, so insecure. Since we don't want unencrypted network traffic from/to your databases, the db-tunnel provides an encrypted way to access them.
Now that we turned on TLS in MongoDB databases, the traffic between your computer and your database at Scalingo's facilities can safely flow without the db-tunnel.
We give you the possibility to open your database to be publicly reachable from the world wild internet. Just head to your database dashboard and click on the toggle button to make it reachable from internet.
Near term future
With the preparatory phase now completed, you can expect replicasets for Scalingo MongoDB really soon.



