VPN IPsec addon: connect your Scalingo apps to your protected infrastructure

Sometimes, your application may need to reach an infrastructure which is not opened to the Internet and the only way to access the services or databases in this infrastructure is to create a VPN connection and join the private network of this infrastructure. This addon provides a way to create VPN connections from your application containers.

Context
The need to access protected infrastructure by VPN has been picked up by our customer MF-TEL and they agree to sponsor the work of developing an addon. You can been very thankful to them because they also agree to let us share this work publicly. They have been using this addon for a few months, and today, we’re making it Generally Available.
What kind of VPN?
Currently, you can connect to a VPN IPSec (Cisco) in mode client-to-site. The addon is using the tool vpnc, so any VPN compatible with this client will be working correctly.
Setup of the addon
Provision the addon
First, you need to provision the add to your application. This can be done through the dashboard or with our command line tool.
scalingo scalingo-vpn-ipsec vpn-ipsec-standard
Setup the configuration
From the addon tab of your dashboard, click on ‘Link to Dashboard’ under the VPN addon icon. You’ll arrive on the dashboard of the VPN IPSec addon. It contains a text area in which you’ve to write your vpnc.conf file.
Usually such configuration file looks like this:
IPSec gateway [server]
IPSec ID [VPN group]
IPSec secret [shared secret]
Xauth username [username]
Xauth password [password]
Once you’ve validated the configuration, the environment variable SCALINGO_VPNC_CONF will be added to your application, the app will be restarted. You’ll be able to see in the logs:
2016-02-03 13:59:31.321065492 +0100 CET [web-1] -----> Starting VPN connection
2016-02-03 13:59:31.321223270 +0100 CET [web-1] -----> VPNC started in background (pid: 70)
Automatic reconnection
Our container runtime will check in real time if anything happens to the connectivity between your Docker container and the VPN it’s connected to. If it is disconnected you’ll see in your application logs:
2016-03-02 19:36:59.95866371 +0100 CET [web-1] ! VPN disconnected, attempt to reconnect
Then, the system will immediately try to reconnect to the VPN. In the reconnection fails because of a problem of your infrastructure, or because of networking problems, we’ll attempt to reconnect every 30 seconds.
How does it work?
Your application is running in one or several Docker containers. By default these containers are connected to the external world with one network interface. When you are using this VPN addon, we automatically create a second network interface used for the VPN connectivity. The following schema represent this method.
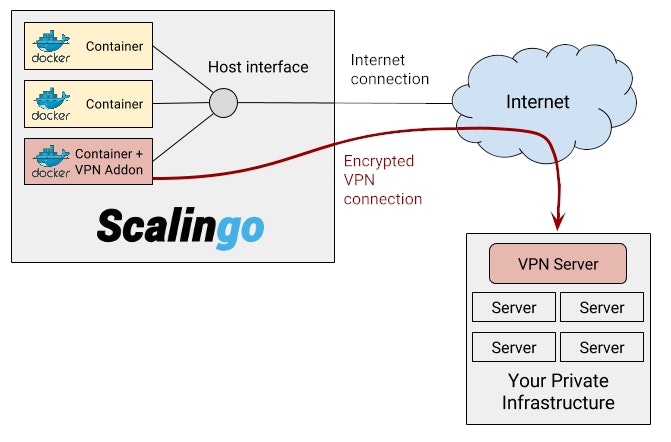
Security consideration
One of the first question you may be asking yourself is: “how safe is it?”. We’re ensuring that the VPN interface is only present inside the network namespace of your application containers. A network namespace is an isolated virtual environment linked to a container. It contains all the network interfaces dedicated to this precise container. It means that for other containers sharing the same host, there is no way to see of sniff anything related to your VPN.
Q&A
- Can I setup site-to-site VPN?
No, currently site-to-site VPN is not compatible with this addon, it is only working in client-to-site mode.
- What happens if the connection fail, will my app be unavailable?
No, it will be written in the logs that we have not been able to connect your container to your VPN, but your application will be started correctly. You should check the configuration and ensure all the fields are correct.
- Where can I find an comprehensive documentation of the
vpnc.conffile?
The Ubuntu manpage about vpnc contains all the properties which can be set in the configuration file.
Conclusion
This addon only contains a single plan. Once provisioned you’ll be able to configure a VPN connection for your app. We’ll see in the future, thanks to your feedback, if additional features or plans are required.
To finish, thanks again MF-TEL for sponsoring the development of this addon!



